The Intelligence Cycle is the process of devel-oping raw information into finished intelligence for use by policymakers military commanders and other consumers in decisionmaking. The descriptions are drawn from what may only be available in the form of deliberately deceptive information.
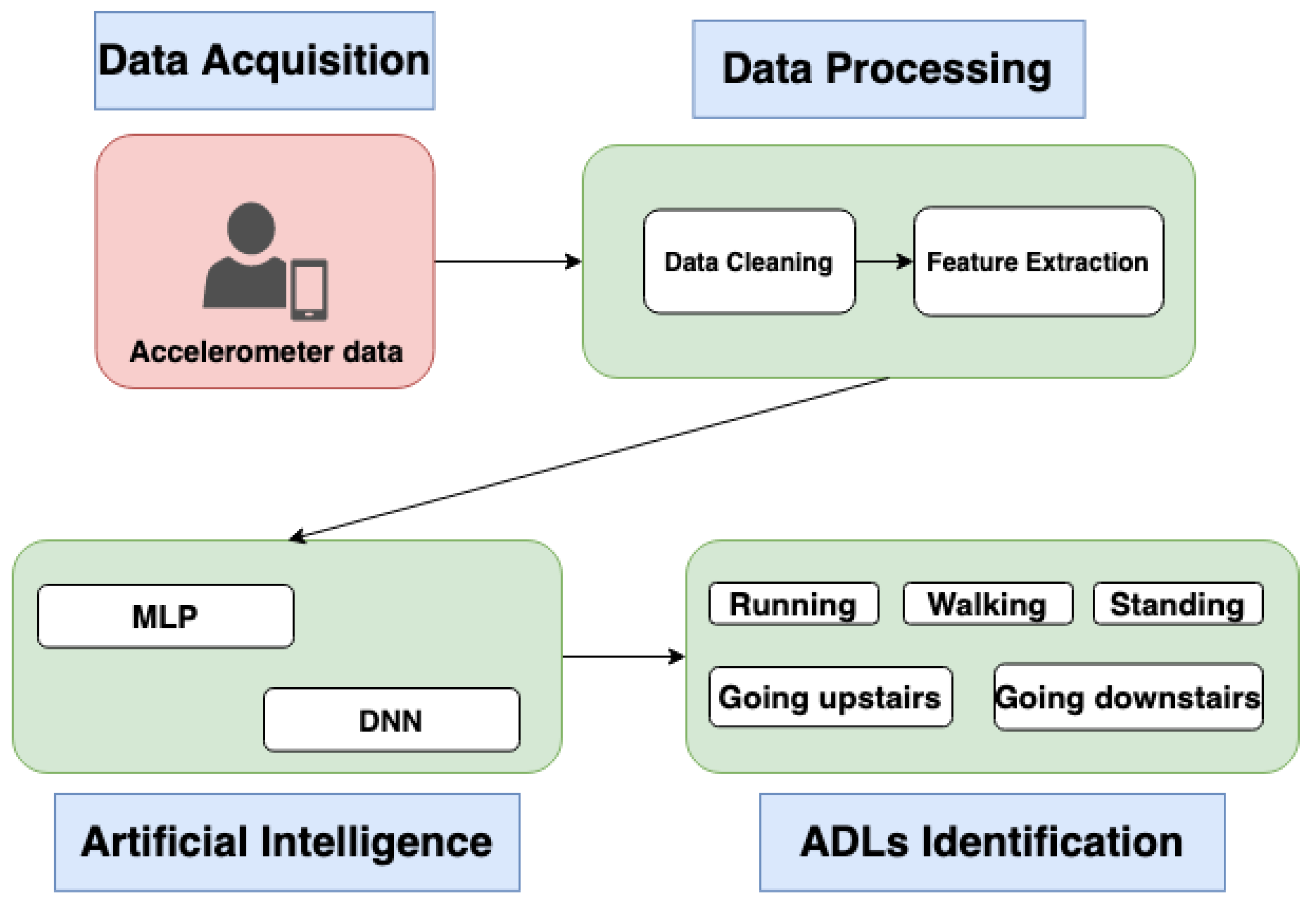
Electronics Free Full Text Pattern Recognition Techniques For The Identification Of Activities Of Daily Living Using A Mobile Device Accelerometer Html
Intelligence operations consist of the functions that constitute the intelligence process.

. The sixth step evaluation which includes soliciting feedback. 6 During this activity in the joint intelligence process raw data is converted into forms that can be readily used by commanders decision makers at all levels intelligence analysts and other consumers. The fusion of the different information that was processed from the different intelligence disciplines.
Phase occurs when the mission is executed and the sensors actually gather raw data on the target set. The collected data in its raw form has relatively limited intelligence utility. Problems with a closed loop include an overall process that is no better than its weakest component and stove piping.
Raw collected data is converted into forms. The cycle is typically represented as a closed path of activities. In this stage also known as data gathering intelligence is acquired through activities such as interviews technical and physical surveillance human source operations searches and liaison relationships.
It is a continuous process that involves four major steps. The analyst must correlate the similarities among deceptions and extract a common truth. The processing and exploitation phase increases the utility of the collected data by converting it into useable information.
What G-2S-2s and Collection Managers Need. This type of command is established on a geographical or functional area with a mission that is limited and specific During this activity in the joint intelligence process raw data is converted into forms that can be readily used by commanders decision makers at all levels intelligence analysts and other consumers. This vital keystone publication form s the core of joint intelligence doctrine and.
Iii SUMMARY OF CHANGES REVISION OF JOINT PUBLICATION 2-03 DATED 31 OCTOBER 2012 Clarifies the national security mission of National Geospatial-Intelligence Agency to include responsibility for analysis dissemination and incorporation of geospatial. This vital keystone. 6 During this activity in the joint intelligence process raw data is converted into forms that can be readily used by commanders decision makers at all levels intelligence analysts and other consumers.
Analysis and production The refinement of the information that was produced in the previous step. This six-step cyclical process is highly dynamic continuous and never-ending. Joint Intelligence Preparation of the Operational Environment JIPOE is the analytical process used by joint intelligence organizations to produce intelligence assessments estimates and other intelligence products in support of the commanders decision-making process.
This revised edition of JP 2-0 Joint Intelligence reflects the current guidance for conducting joint and multinational intelligence activities across the range of military operations. Joint force commanders must perform an analysis of the adversary known as a _____ to know what actions will be an effective deterrent. Intelligence Activities states that when an intelligence pro-fessional copies stores or otherwise preserves something into an intelligence component database they have con-ducted an OSINT collection activity5 For most all-source an-alysts suddenly becoming a collector is a radical change.
Joint and multinational intelligence activities across the range of military operations. Objective89 Remediation Accessed N Collection Dissemination and Integration Processing and Exploitation Analysis and Production. This continuous analytical process is used by joint intelligence organizations to produce intelligence estimates and other intelligence products in support of the commanders decision-making process.
The Joint Intelligence Process The joint intelligence process provides the basis for common intelligence. During the analysis and production phase. In addition the Intelligence.
These are key tasks performed during this step. Information can be gathered from open covert electronic and satellite sources. Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context.
Evaluating interpreting and integrating raw processed and exploited data and information into intelligence products for known or anticipated purposes and applications. Gathering raw information from many different sources. In the Coast Guard intelligence staffs perform analysis and develop products for their supported commanders.
1 defining the total operational. Intelligence therefore is at once inseparable from both command and operations. Select all that apply objective88 visualize and understand all dimensions of the OE understand adversary capabilities and intentions support a predictive estimation of the situation _____ 6 During this activity in the joint intelligence process raw data is converted into forms that can be readily used by commanders decision makers at all.
Collection activities acquire and extract data from the operational environment such that Processing and Exploitation can convert that data into information to be used during Analysis and Production to refine into _____ to satisfy Requests for Information RFI or the commanders Priority Intelligence Requirements PIR. The Intelligence Cycle is a concept that describes the general intelligence process in both a civilian or military intelligence agency or in law enforcement. The raw data becomes information.
Plan prepare collect process produce and the three common tasks of analyze disseminate and. Intelligence contributes to the exercise of effective command during military operations and helps ensure the success-.
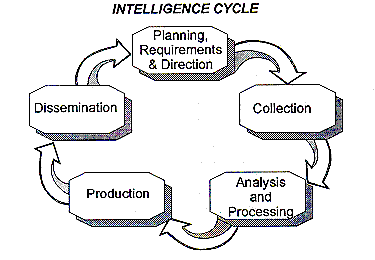
Section 2 Intelligence Collection Activities And Disciplines Operations Security Intelligence Threat Handbook
0 Comments